
I wish you all a Prosperous and Happy New Year 2008.
Bharath M N

Posted by Bharath M Narayan at 8:11 AM View Comments

Posted by Bharath M Narayan at 1:35 AM View Comments

Posted by Bharath M Narayan at 12:16 AM View Comments
Posted by Bharath M Narayan at 12:02 AM View Comments

BHO Details:
Filename: IECodec.dll
Hijack this entry:
O2 - BHO: IECodecBHO - {4507C219-24AA-4813-9561-A2003F9920C3} - C:\Program Files\IECodec\IECodec.dll
Screeenshot taken after installing the malicious setup file.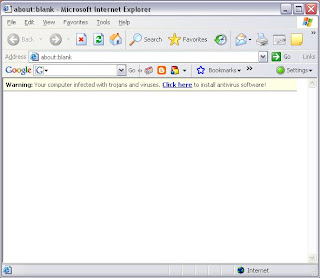
Stay away from these sites.
Bharath M N
Posted by Bharath M Narayan at 5:34 AM View Comments

Yet another Spysheriff Clone. This site distributes Rogue security application. The application exploits “Webroot” Spy-sweeper name.
Snapshot of Spyware-Sweeper Application

Posted by Bharath M Narayan at 3:19 AM View Comments






Posted by Bharath M Narayan at 11:55 PM View Comments


Posted by Bharath M Narayan at 7:10 PM View Comments
Stopingspy.com

Posted by Bharath M Narayan at 9:00 PM View Comments
 This is a new rogue security application which is successor of IE Defender Rogue security application. The AntiSpy-Pro is an exact clone of IE Defender rogue security application.
This is a new rogue security application which is successor of IE Defender Rogue security application. The AntiSpy-Pro is an exact clone of IE Defender rogue security application.
Posted by Bharath M Narayan at 4:34 PM View Comments
Posted by Bharath M Narayan at 6:50 PM View Comments

Guard-center.com
Application Screen Shot of Guard-center
Liveantispy.com
Application Screen Shot of Liveantispy


Posted by Bharath M Narayan at 5:59 PM View Comments

Posted by Bharath M Narayan at 12:38 AM View Comments
Posted by Bharath M Narayan at 11:48 PM View Comments

Usually the porn sites use the following fake alert to goad the user into downloading the fake video decoder.

ElseIf.biz uses the IP Address: 85.255.121.148; Detection of the download from this site is really poor. Stay away from malicious porn sites.
Avoid the site and all its downloads…
The website's name reminds me of the collage days where in we coded in C-language :-)
Code:
if(You are sensible not to download and install codec promoted by porn site)
{
Your system is safe and you need not worry about the Zlob Trojan infection
Exit from the porn trap;
}
else if(you install the codec)
{
Welcome to the world of Zlob infected PC's;
The Trojan will make sure to make you have a terrible experience;
Use tool to remove the infection;
Make a promise never to install a codec pushed from a porn site;
Finally exit from the porn trap;
}
else
{
Wait until the bad guys comes up with a new trick to trap you;
goto CODE
}
Isn’t it a funny code :-)
Bharath MN
Posted by Bharath M Narayan at 1:51 AM View Comments

Yet another Rogue Security application from SpyLocked group of Rogue security application.
VirProtect is the latest entry to the list; This Rogue is currently advertised by the latest Zlob Trojan. The site uses the IP 85.255.119.126 which is also used by virusray.com (Previous rogue security application released from this group)
Screenshot of the application.

Detection of the rogue is poor.
VirusTotal Scan Result: 7/31 (22.59%)
Avast 4.7.1074.0 2007.11.13 Win32:Spycrush-B
BitDefender 7.2 2007.11.13 Adware.SpyLocked.C
Ikarus T3.1.1.12 2007.11.13 Virus.Win32.Spycrush.B
Kaspersky 7.0.0.125 2007.11.13 not-a-virus:FraudTool.Win32.VirusProtectPro.h
Microsoft 1.3007 2007.11.12 Program:Win32/VirusLocker
Rising 20.18.11.00 2007.11.13 Hack.Win32.VirusProtectPro.a
VBA32 3.12.2.4 2007.11.11 Application.Win32.Adware.VirusProtectPro
Avoid it at all cost…
Bharath M N
Posted by Bharath M Narayan at 12:06 AM View Comments


Posted by Bharath M Narayan at 2:54 AM View Comments
Posted by Bharath M Narayan at 2:28 AM View Comments


The site uses the IP 84.243.253.220 which is also used by many other Sellmosoft Inc Rogue Security Application.
Some of the other Rogue security applications that used/uses this IP are:
1. Performanceoptimizer.com
2. Antivirussecuritypro.com
3. Cryptdrive.com
4. Windefender.com
and many more. Detection on Virustotal is really poor.
Avoid it at all cost...
Bharath M N
Posted by Bharath M Narayan at 8:14 PM View Comments


The application is aggressively advertised by Zlob Trojans. When a System gets infected by a Zlob Trojan you might receive the following warning message or a similar warning message luring /confusing/goading users to purchase any one of the many AVSystemcare clone application.


Avoid all the sites...
Posted by Bharath M Narayan at 2:19 AM View Comments
Posted by Bharath M Narayan at 11:19 PM View Comments

This is a new scam that uses the windows Messenger Service to exploit the users into purchasing the rogue security application.
“The scam popup indicates that your computer is vulnarable to pop-ups, viruses, hackers, crackers, unwanted advertisement, spam, etc.”
This scam is directed to scare the users into purchasing the unwanted application to solve the problem.
CA and Symantec have a detail description about the rogue security application.
Avoid the sites and the application that it promotes.
Bharath M N
Posted by Bharath M Narayan at 3:22 AM View Comments

Posted by Bharath M Narayan at 2:50 AM View Comments


Posted by Bharath M Narayan at 7:08 PM View Comments